Access control installation is an important decision for businesses of all sizes. Whether you run a small mom-and-pop shop or a large, high-traffic office building, installing the type of access system you need (and doing so affordably) is a must. One popular solution is installing door card reader systems. These systems not only enhance security but also provide the convenience of allowing authorized personnel to enter restricted areas with just a swipe or tap of a card.
The door card reader installation process can be daunting though, especially for businesses on a tight budget. Fear not! This article will guide you through cost-effective door card reader installation tips, making sure you get the most bang for your buck without compromising on quality or security.

What you will learn:
- About Various Card Reader Systems
- What To Consider Before Installation
- Access Control Door Card Reader Pros And Cons
- Common Myths About Card Readers
- 7-Step Guide To Reader Installation (Diagram PDF Download)
- FAQs
Understanding Door Card Reader Systems
Before we dive into the installation process, let’s first understand the basics of door card reader systems. These systems typically consist of three main components:
- the card reader itself
- an access control panel
- the door lock
The card reader is the device mounted near the door, where users present their access cards. It communicates with the access control panel, which acts as the main brain of the system, verifying the credentials and controlling the door lock accordingly.

There are several different types of card readers on the market, such as:
- proximity readers
- smart card readers
- biometric readers
Proximity readers are the most common and cost-effective option, allowing users to simply wave their card near the reader. Smart card readers offer enhanced security by requiring the user to insert the card and enter a PIN. Biometric readers, like fingerprint scanners, provide the highest level of security but can be more expensive.
Planning to Install Access Control?
As a business owner, you must assess your facility’s needs and requirements before starting the installation. First, determine the number of access points that require card reader systems and identify the most suitable locations for the readers.
Consider factors such as traffic flow, visibility, and accessibility. Also, remember to keep in mind future expansion plans to ensure scalability. You need to make sure that your system can grow with your business.

Finding Cost-Effective Hardware When Installing Access
One of the most significant expenses in door card reader installation is the hardware itself. To keep costs down, explore different card reader models and compare prices and features. Look for reputable brands that offer reliable and cost-effective solutions. If your building already has an existing access control system, see if you can partner with a security company to reuse your old system. This can be a great way to maximize your company’s initial investment.
While choosing the right hardware is important, don’t forget about the software side either. When it comes to access control software and databases, you need something that is going to accommodate to your needs, while still being budget-friendly. Think of the features your business will use most. Is simple, remote user management a must-have? Then you might need a cloud-based solution with an easy to use phone app. Make sure to carefully evaluate the features, support, and security of any software you choose. If that’s too overwhelming, then partner with a trusted security company who can help you find the right solution.
Final Things To Consider Before Install
Proper installation is the first step toward an effective door card reader system. Before installation, make sure to prepare your site including running wires and identifying a power supply for the components. Mounting locations should be carefully selected to provide optimal usability and minimize tampering or vandalism risks. If you have any existing security or access control systems, it’s important to consider integration during the installation process too.

- DIY or Professional Installation? One of the biggest cost-saving opportunities lies in deciding whether to tackle the installation yourself (DIY) or hire professional installers or contractors. DIY installation can be a viable option for those with technical expertise and experience in similar projects. However, it’s important to carefully weigh the potential risks and consequences of improper installation, such as compromised security, issues with the system, and failure to meet regulations. If you decide to go the DIY route, be sure to thoroughly research the installation process, follow manufacturer instructions to the letter, and invest in the necessary tools and equipment. On the other hand, hiring professional installers or contractors can provide peace of mind and ensure a smooth, reliable installation. While this option may be more expensive upfront, it can save you time, effort, and potential headaches or security risks down the line. Professional installers are trained experts in all things access control and door card reader systems. Plus, having professionals on your side helps you to troubleshoot any issues that may arise.
- Testing and Troubleshooting. Speaking of troubleshooting, thorough testing is crucial to make sure that an access control system and its various components are functioning as intended. Regular maintenance and updates are also essential to keep your door card reader system running smoothly and securely. Stay on top of software updates, firmware upgrades, and hardware maintenance to ensure optimal performance and address any potential vulnerabilities. Common installation issues may include wiring problems, software configuration errors, or hardware malfunctions. If you encounter any issues during testing or operation, don’t panic! Many common problems can be resolved through troubleshooting. Consult the manufacturer’s documentation, or reach out to an access control company near you for guidance.
Pros and Cons of Door Card Readers
Like any other security solution, door card reader systems come with their own set of pros and cons. Let’s explore some of the key advantages and disadvantages of a card-based access system:
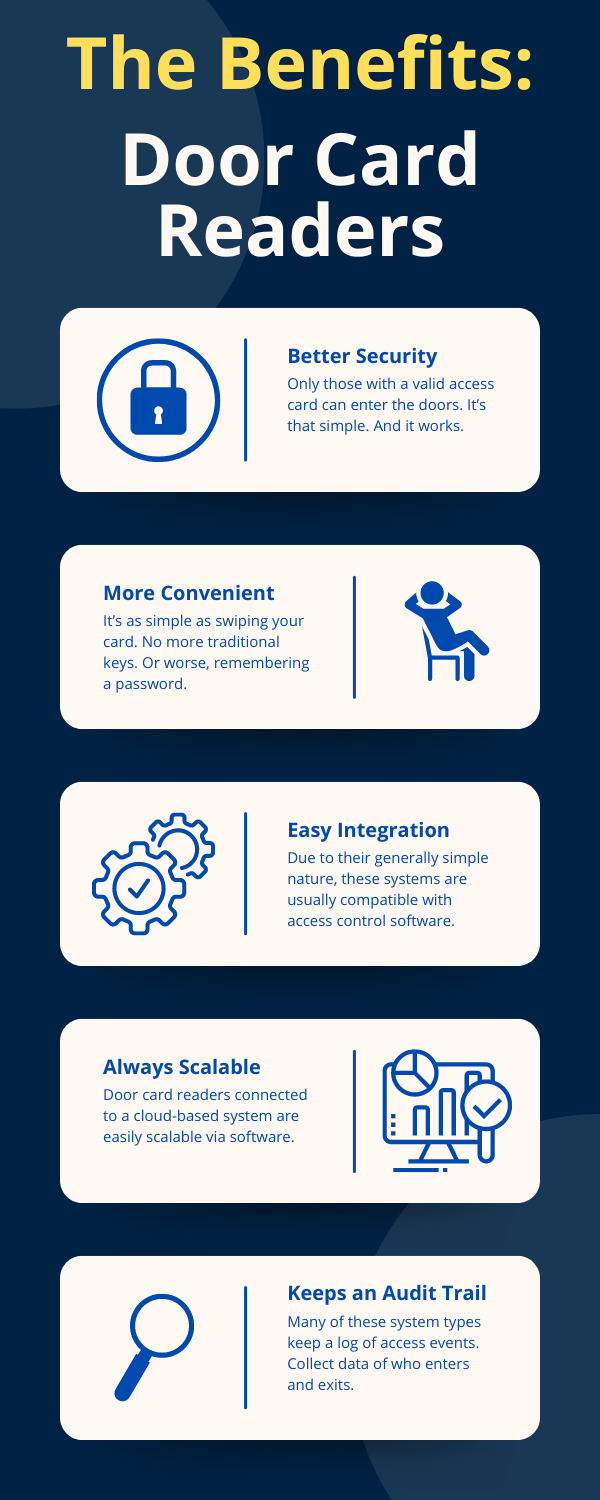
The Pros:
- Enhanced Security: Door card reader systems provide an additional layer of security by restricting access to authorized personnel only. This can help prevent unauthorized entry, theft, and other security breaches.
- Convenience: With a simple swipe or tap of a card, authorized individuals can gain access to restricted areas without the need for traditional keys or memorizing complex codes.
- Access Control and Monitoring: Most door card reader systems integrate with access control software, allowing you to monitor and manage who has access to specific areas and at what times.
- Scalability: The right door card reader system can be easily expanded or modified as your business grows or your security needs change.
- Audit Trail: Many systems keep detailed logs of access events, providing a valuable audit trail for security and compliance purposes.
The Cons:
- Initial Cost: The initial investment in hardware, software, and card reader installation can be substantial, especially for larger facilities with multiple access points.
- Maintenance and Upgrades: Like any technology, door card reader systems require regular maintenance, software updates, and hardware replacements, which can add to the overall cost over time.
- Potential for Misuse or Theft: Access cards or credentials can be lost, stolen, or shared, potentially compromising the security of the system.
- Power Outages: In the event of a power outage, some systems may not function properly, leaving access points vulnerable until power is restored.
- Training and Adoption: Implementing a new access control system may require training for employees and a period of adjustment as they adapt to the new procedures.

Common Myths About Door Card Readers Install

Having been in the industry for so long, we have heard many myths and misconceptions surrounding door card reader installation. Let’s debunk some of the most common ones:
- Myth 1: Door card reader systems are too expensive for small businesses. Reality: While enterprise-level systems can be costly, there are many cost-effective options available for small businesses.
- Myth 2: Installing a door card reader system is too complex and technical. Reality: While the installation process does require some technical knowledge, hiring professional installers can take the complexity out of the equation.
- Myth 3: Door card reader systems are easy to bypass or hack. Reality: Modern door card reader systems are highly encrypted. When properly installed and maintained, they can provide some of the best security against unauthorized access.
- Myth 4: Once installed, door card reader systems require little to no maintenance. Reality: Regular maintenance, software updates, and hardware replacements are crucial to ensure the continued security and reliability of your system. Neglecting maintenance can leave your system vulnerable to security breaches or malfunctions.
- Myth 5: Door card reader systems are only suitable for large facilities or high-security environments. Reality: Door card reader systems can benefit businesses of all sizes and across various industries. They enhance security, make locking and unlocking easier than ever, and can even provide insights into employee and customer movements.
Step-by-Step Guide to Access Control Reader Installation

Now that we’ve covered the basics, let’s dive into a step-by-step guide for installing a door card reader system. Remember, this is a general guide, and it’s always best to consult the manufacturer’s specific instructions for your system.
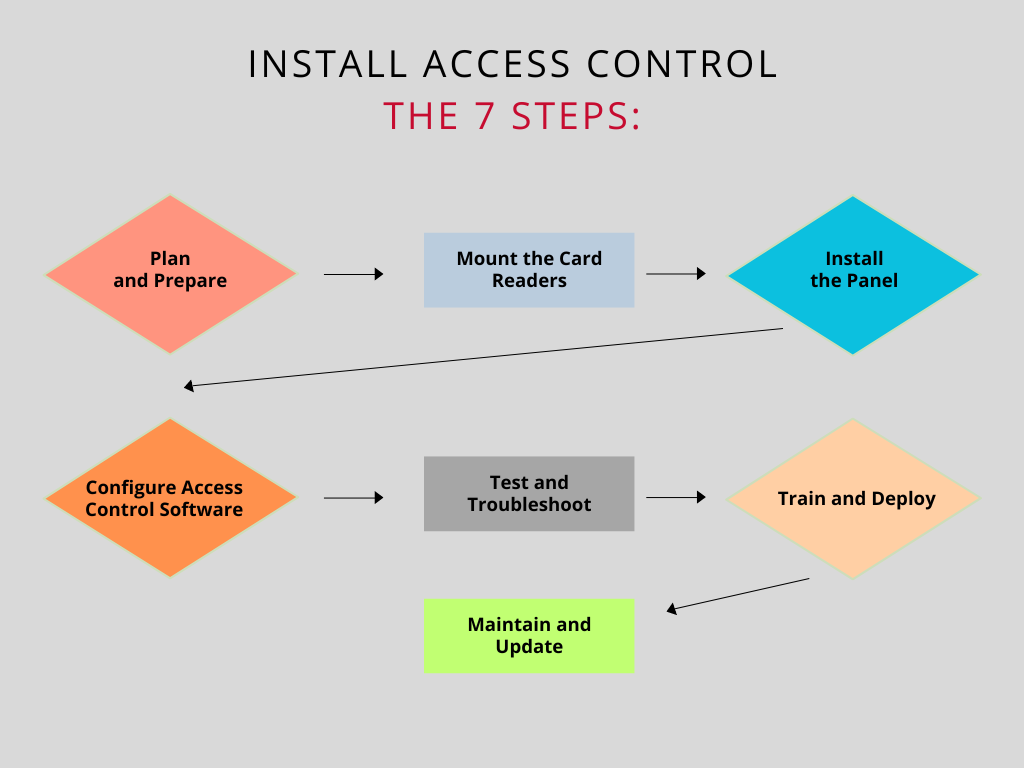
Download 7-Step Guide Diagram PDF
Step 1: Plan and Prepare
- Assess your facility’s needs and determine the number of access points requiring card readers.
- Choose the appropriate card reader type (proximity, smart card, etc.) based on your security requirements and budget.
- Select a suitable access control panel and software that meets your needs and integrates with your chosen card readers.
- Gather all necessary equipment, tools, and materials for the installation.
- Ensure you have adequate power sources and wiring in place for the components.
Step 2: Mount the Card Readers
- Identify the optimal mounting locations for the card readers, considering factors such as traffic flow, visibility, and accessibility.
- Follow the manufacturer’s instructions for properly mounting the card readers, ensuring a secure and level installation.
- Run the necessary wiring from the card readers to the access control panel, using appropriate cable management techniques.
Step 3: Install the Access Control Panel
- Choose a secure and accessible location for the access control panel, such as a server room or a dedicated access control closet.
- Mount the panel securely, following the manufacturer’s instructions.
- Connect the wiring from the card readers to the appropriate terminals on the access control panel.
- If required, install any additional components like power supplies, backup batteries, or network connections.
Step 4: Configure the Access Control Software
- Install the access control software on a dedicated computer or server, following the manufacturer’s guidelines.
- Configure the software to recognize and communicate with the installed card readers and access control panel.
- Set up user accounts, access levels, and permissions based on your security requirements.
- Create schedules and rules for when and where specific users can gain access.
- Integrate the access control system with other security systems (e.g., video surveillance cameras, alarm system) if applicable.
Step 5: Test and Troubleshoot
- Before going live, conduct thorough testing of the entire system to ensure everything is working as intended.
- Follow the manufacturer’s recommended testing procedures and document any issues.
- Troubleshoot any problems that arise, consulting the documentation, online resources, or professional support if needed.
- Verify that all components are communicating correctly and that access rules and permissions are as desired.
Step 6: Train and Deploy
- Develop training materials and procedures for employees on how to use the new door card reader system.
- Conduct training sessions to ensure everyone understands the proper usage and security protocols.
- Distribute access cards or credentials to authorized personnel.
Step 7: Maintain and Update
- Implement a regular maintenance schedule for the door card reader system, including hardware inspections, software updates, and firmware upgrades.
- Keep up-to-date with the latest security best practices and industry standards to ensure your system remains secure and compliant.
- Plan for future expansions or upgrades as your business grows or security needs evolve.
FAQs
How much does it cost to install a card reader?
You can expect to spend up to $5000 when installing a door card reader. If there is an existing system involved and you are reusing equipment that can cut down costs. Depending on the type of setup, you can put an access control system in place for $500 to $2000 per door on the lower end. For access control installation, it is wise to get a quote from a professional access control company.
How far should a card reader be from the door?
Simply put, RFID readers should be installed 48″ from the floor at a maximum.
Does access control installation require training?
Like with any new hardware, access control installation requires training for those installing and maintaining the system, as well as for employees who will be using the system on a regular basis. Access control training should include required reading and study materials, as well as hands-on training with the hardware.
What are the most popular access control brands?
Some of the most common access control brands include: Brivo, Genetec, HID, 3xLogic, Napco, DSC, Ademco, Interlogix, Verkada, Avigilon, Honeywell, Bosch, Lenel S2, Johnson Controls, and Alarm.com. Alarm New England’s access control technicians have experience with these brands and can help you reuse your system for a more affordable setup.
Save Money While Installing Your Door Access System!
Installing a door card reader system can be a significant investment, but by following these cost-effective tips, you can ensure a secure and reliable solution without breaking the bank.
Remember, while cost is an important factor, it should never compromise the security and reliability of your access control system. Business security and safety should not be a headache. Professional installers are here to make it easy. By taking the time to research and plan an installation, you can enjoy the benefits of enhanced security, convenience, and peace of mind for years to come.

Get in Touch
If you’ve been dreading the process of installing access control, you don’t need to fear. With the help of an experienced access control company, the process is made easy. And if you end up reusing your equipment, that can lead to some serious savings. If any issues arise, service professionals will be on standby ready to address any access control issues. For more information on access control system types, take a look at our guide here.
For further assistance in the process, and to get the ball rolling with an affordable access control system, get in touch with an member of the Alarm New England sales team!